Research Themes
Adversarial Machine Learning
Software Vulnerability Discovery
Advanced Malware Detection
Internet Traffic Classification
Twitter Spam Detection
Security Incident Prediction and Discovery
Insider Attack Detection
Security Key Management
Cyber Security Visualisation
Andriod System Security
Explanalbe System Security
Psycho-cybersecurity for Systems
Risk Assessment on Cyber Physical Systems
Applied Blockchain System
Andriod System Security
Explanalbe System Security
Psycho-cybersecurity for Systems
Risk Assessment on Cyber Physical Systems
Applied Blockchain System
Projects
We have received funding from the Australian government, universities, and our industry partners. The ARC projects that we have received in the last five years are listed as follows.
Modelling and defence against malware propagation
Wanlei Zhou and Yang Xiang
ARC Discovery Project DP140103649, 2014-2016.
Developing an active defence system to identify malicious domains and websites
Yang Xiang, Wanlei Zhou, Vijay Varadharajan, and Jonathan Oliver
ARC Linkage Project LP120200266, 2012-2015.
Developing an environmentally friendly, low cost solution to reduce wear and improve productivity in metal forming
Bernard F. Rolfe, Peter D. Hodgson, Maria Forsyth, Yong Xiang, Matthew C. Doolan, and Michael P. Pereira
ARC Linkage Projects LP120100239, 2012-2014.
Blind separation of mutually correlated sources
Yong Xiang and Yue Rong
ARC Discovery Projects DP110102076, 2011-2013.
An active approach to detect and defend against peer-to-peer botnets
Wanlei Zhou and Yang Xiang
ARC Linkage Project LP100100208, 2010-2012.
Secure and efficient communication in vehicle-based radio frequency identification systems
Wanlei Zhou and Robin Doss
ARC Linkage Project LP100100816, 2010-2012.
Tracing real Internet attackers through information correlation
Yang Xiang, Wanlei Zhou, and Yong Xiang
ARC Discovery Project DP1095498, 2010-2012.
Blind signal separation from unidentifiable systems
Yong Xiang and Hieu Trinh
ARC Discovery Project DP0773446, 2007-2009.
Development of methods to address internet crime
Wanlei Zhou and Yang Xiang
DP0773264, 2007-2009.
Developments
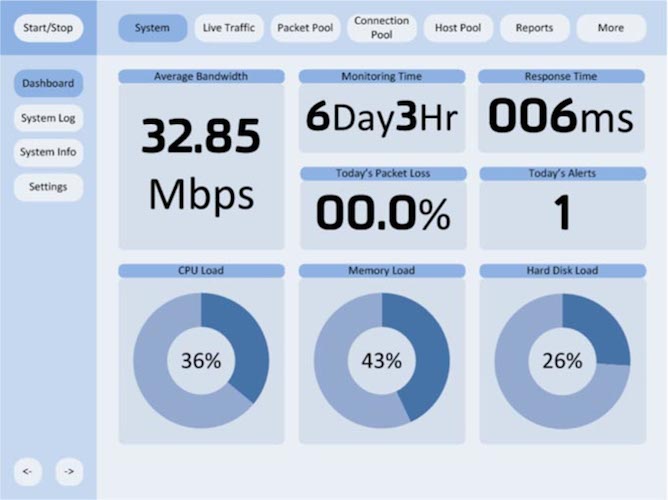
Network Analytics
Accurate and efficient network traffic classification based on our latest research outcomes.
Resources
Network Traffic Data
Accurate and efficient network traffic classification based on our latest research outcomes.
Twitter Spam Data
Accurate and efficient network traffic classification based on our latest research outcomes.