ACISP 2020
25th Australasian Conference on Information Security and Privacy
30 Nov - 02 Dec 2020
30 Nov - 02 Dec 2020
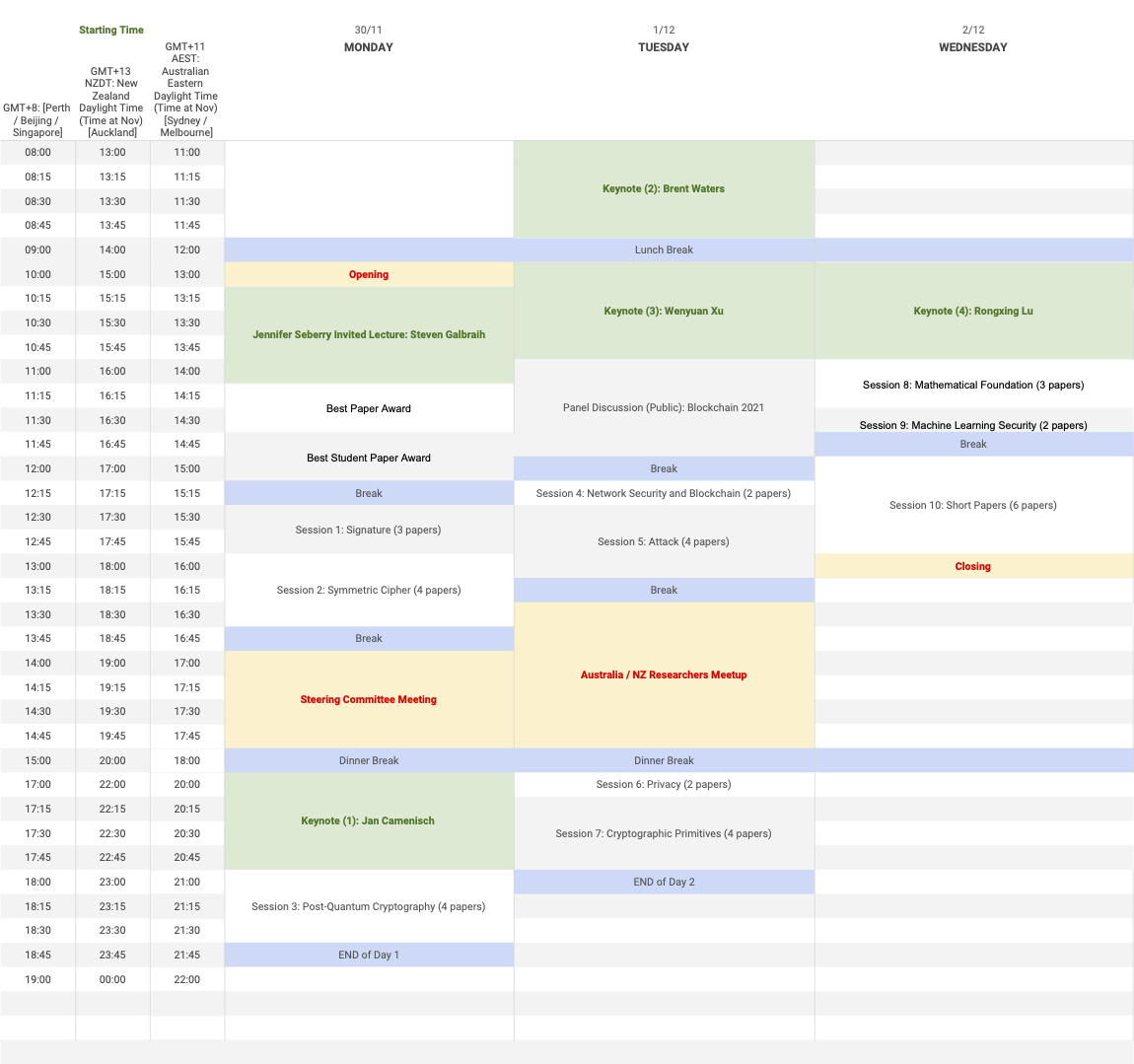
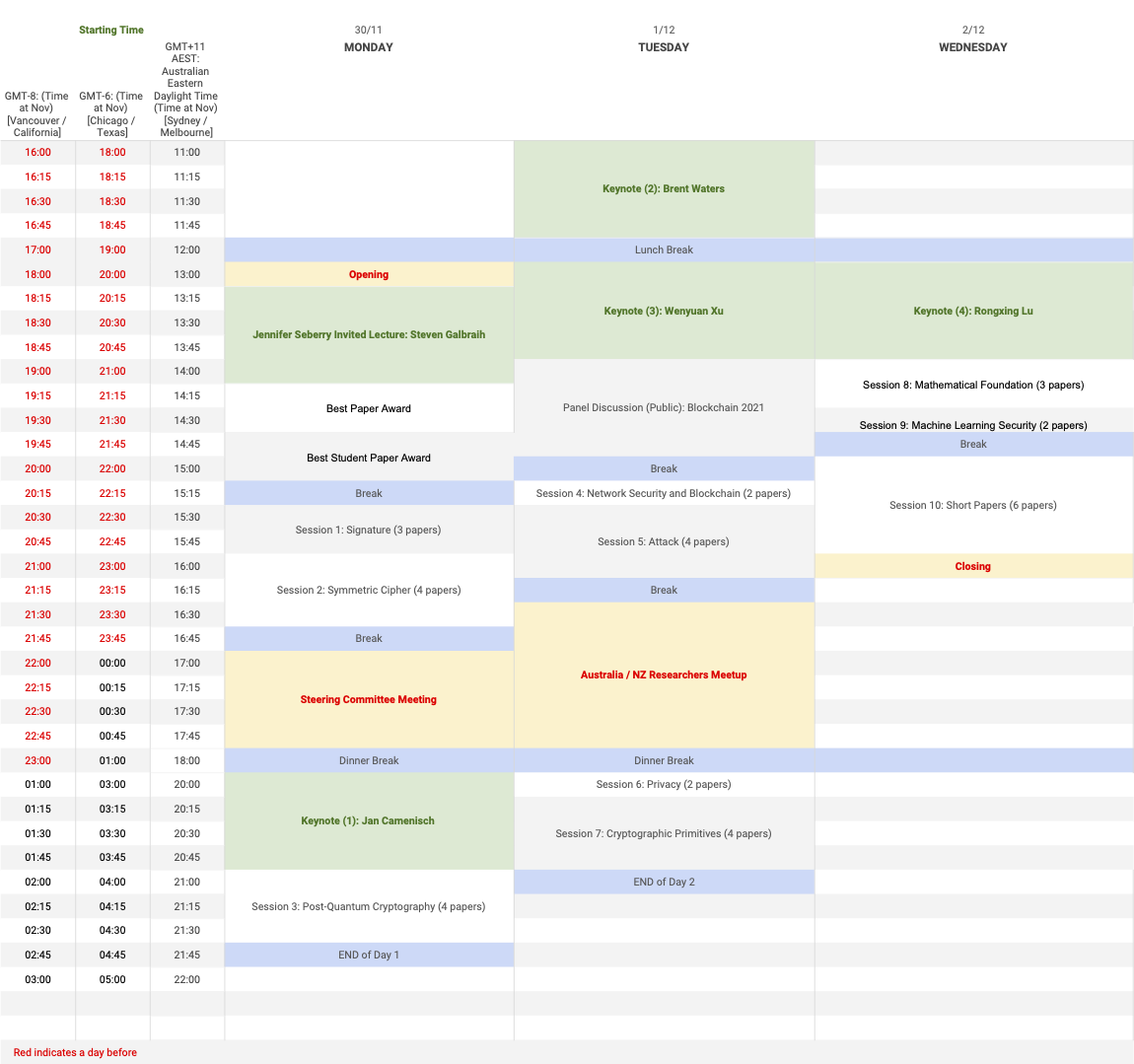
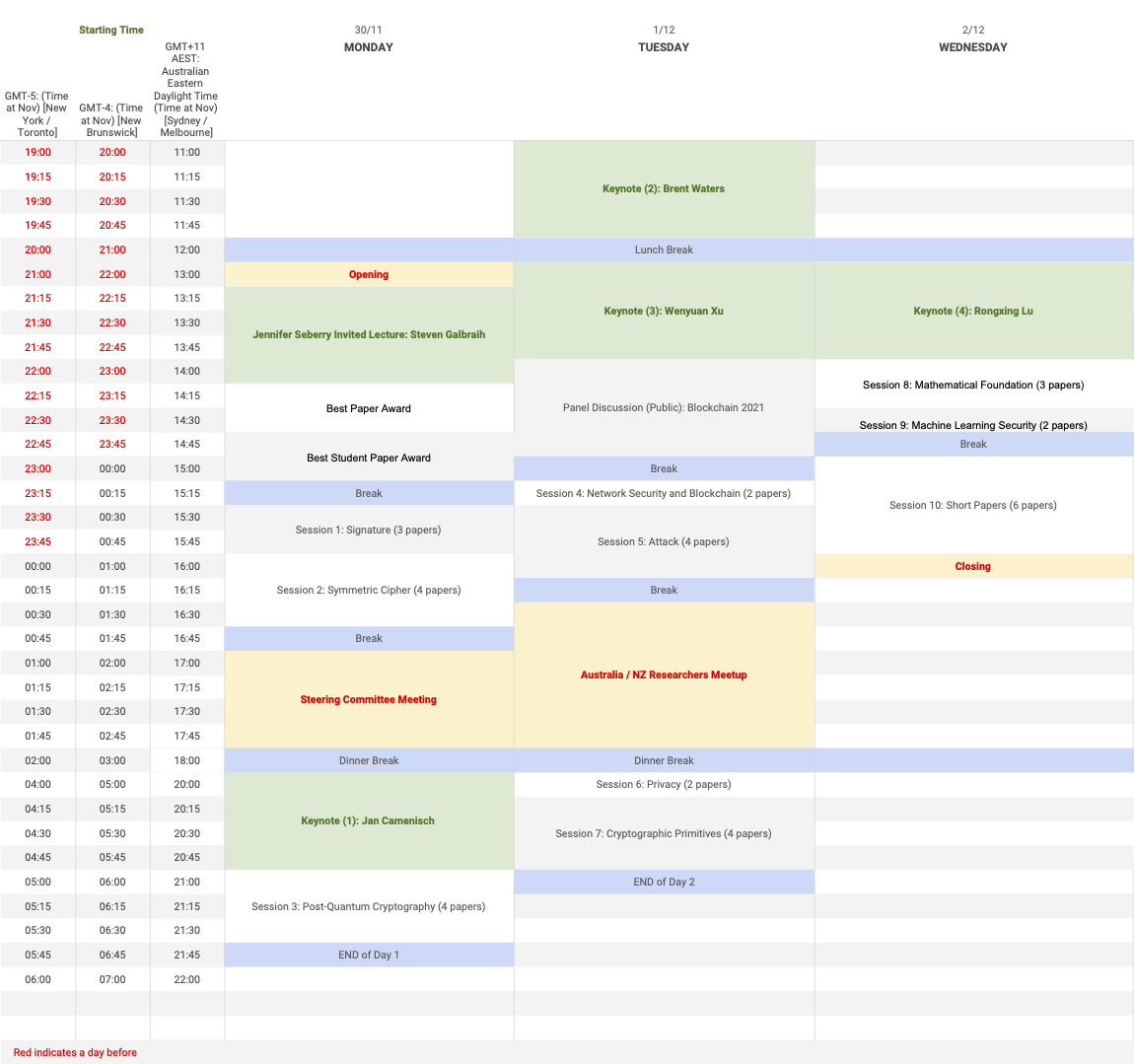
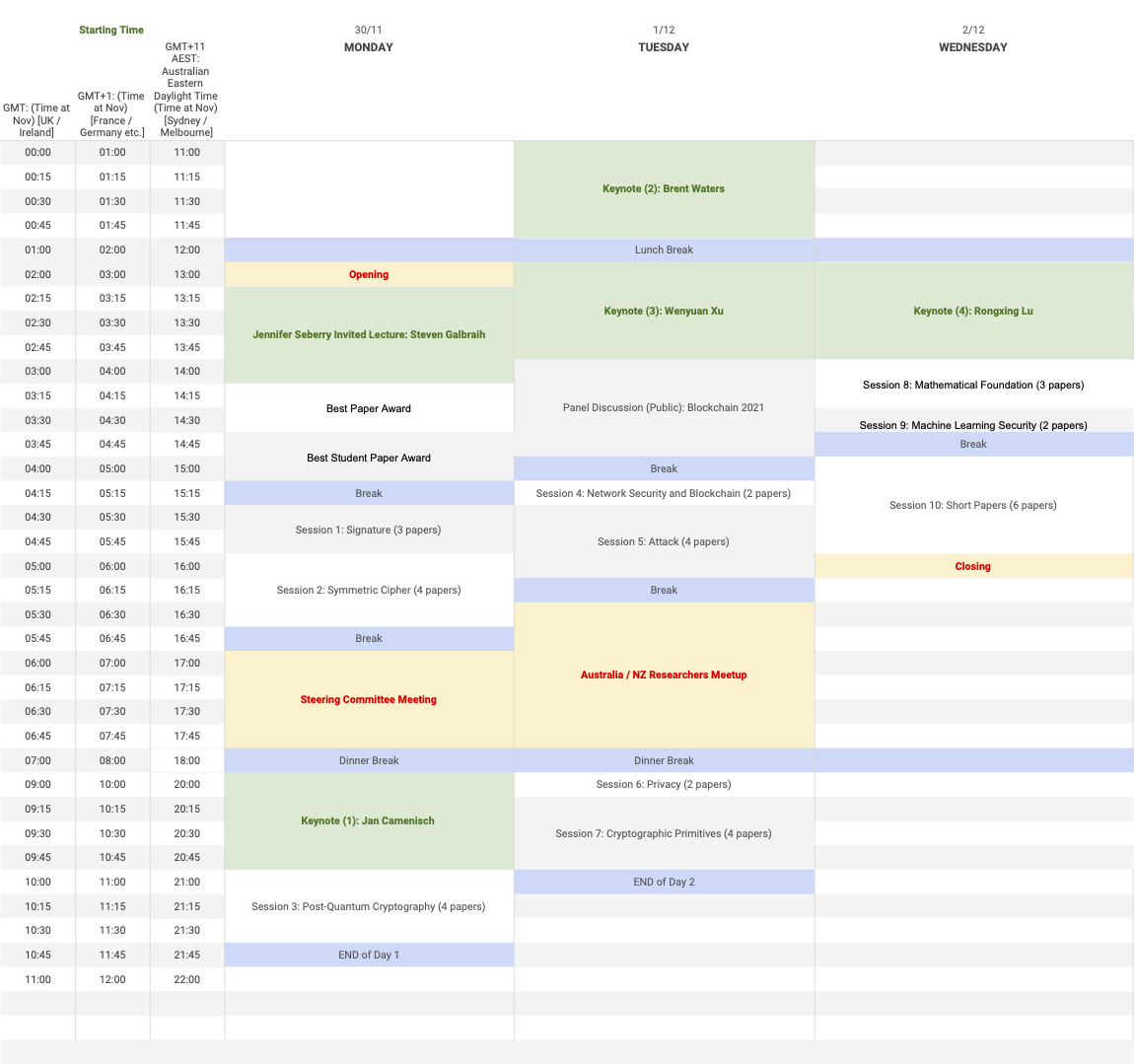
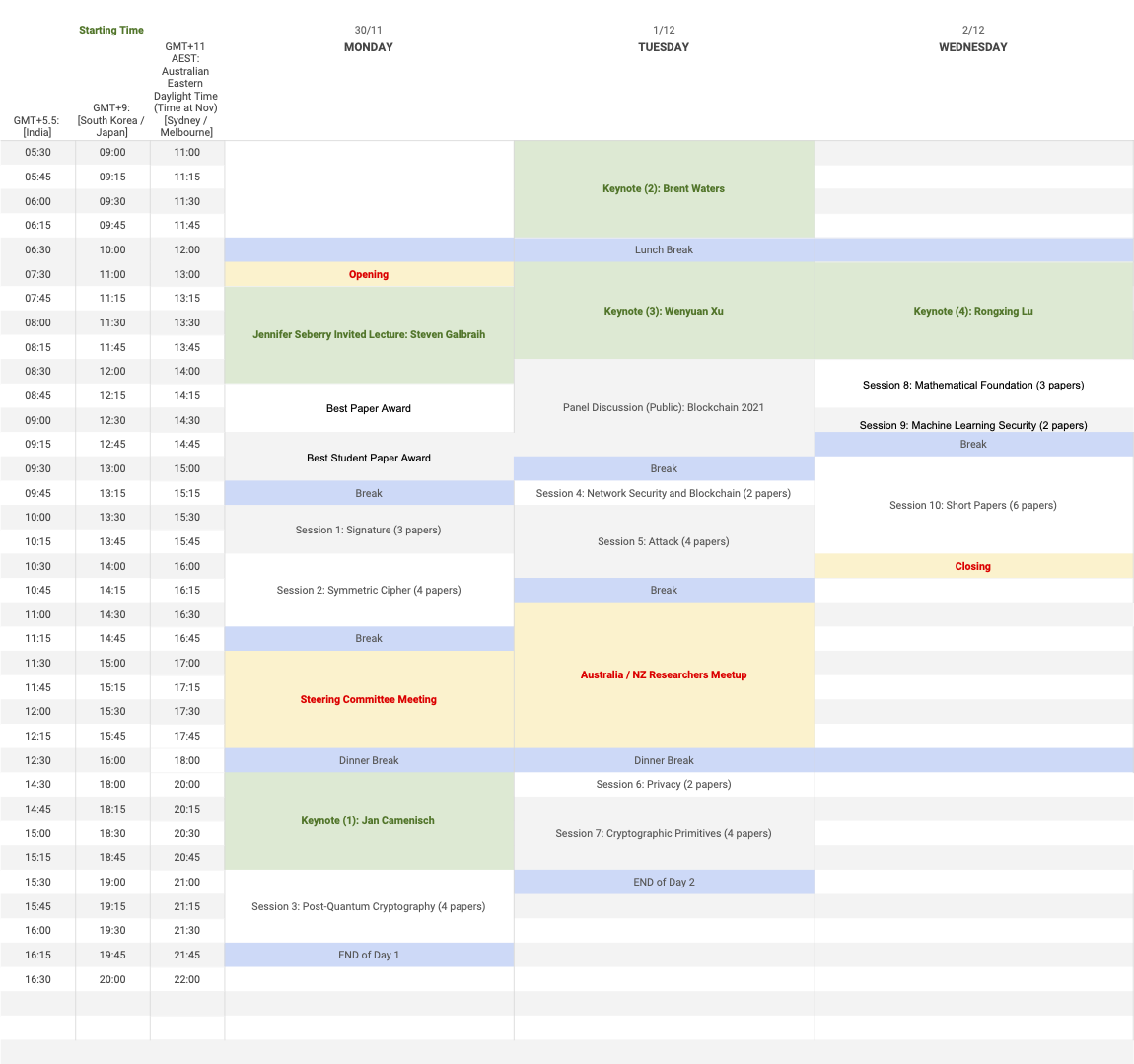
ACISP 2020 Agenda
Australia_NZ_China Time
Central_West_US_CA Time
East_US_CA Time
Europe Time
India_JP_KR Time
Session Details
Keynote and Panel Sessions
Jennifer Seberry Invited Lecture
Session Chair: Willy Susilo
|
Security levels in cryptography
Steven Galbraith Mathematics Department, University of Auckland, New Zealand |
Keynote (1)
Session Chair: Joseph Liu
|
The Internet Computer: Evolution of Cryptography
Jan Camenisch DFINITY, Switzerland |
Keynote (2)
Session Chair: Ron Steinfeld
|
Chosen Ciphertext Security from Trapdoor Functions
Brent Waters Department of Computer Science, The University of Texas at Austin, US |
Keynote (3)
Session Chair: Weizhi Meng
|
A sound story — Analog security of Embedded Systems
Wenyuan Xu College of Electrical Engineering, Zhejiang University, China |
Keynote (4)
Session Chair: Amin Sakzad
|
On Feasibility and Limitations of Detecting False Data Injection Attacks on Smart Grids Using D-FACTS Devices
Rongxing Lu Faculty of Computer Science, University of New Brunswick, Canada |
Panel Discussion
Session Chair: Joseph Liu
|
Blockchain 2021
Man Ho (Allen) Au (University of Hong Kong, Hong Kong) Qiang Tang (New Jersey Institute of Technology, US) Jing Chen (Algorand, US) Jiangshan Yu (Monash University, Australia) |
Best Paper Sessions (for each paper 25 min presentation + 5 min Q&A)
Best Paper Award
Session Chair: Hui Cui
|
Lattice Blind Signature with Forward Secrecy video
Huy Quoc Le (University of Wollongong, Australia) Dung Hoang Duong (University of Wollongong, Australia) Ha Thanh Nguyen Tran (Concordia University of Edmonton, Canada) Viet Cuong Trinh (Hong Duc University, Canada) Thomas Plantard (University of Wollongong, Australia) Willy Susilo (University of Wollongong, Australia) Josef Pieprzyk (Data61, Australia) |
Best Student Paper Award
Session Chair: Hui Cui
|
DCONST: Detection of Multiple-Mix-Attack Malicious Nodes Using Consensus-based Trust in IoT Networks video
Zuchao Ma (Nanjing University of Aeronautics and Astronautics, China) Liang Liu (Nanjing University of Aeronautics and Astronautics, China) Weizhi Meng (Technical Universtiy of Denmark, Denmark) |
All Other Sessions (for each paper 5 min presentation + 5 min Q&A)
Session 1 - Signature
Session Chair: Veronika Kuchta
|
From Rerandomizability to Sequential Aggregation: Efficient Signature Schemes Based on SXDH Assumption video
Sanjit Chatterjee (Indian Institute of Science, India) R Kabaleeshwaran (Indian Institute of Science, India) |
|
Lightweight Implementation of SM2 Elliptic Curve on Intel Processor with AVX2 video
Junhao Huang (Nanjing University of Aeronautics and Astronautics, China) Zhe Liu (Nanjing University of Aeronautics and Astronautics, China) Zhi Hu (Central South University, China) Johann Großschädl (University of Luxembourg, Luxembourg) |
|
Improved Security Proof for the Camenisch-Lysyanskaya Signature-Based Synchronized Aggregate Signature Scheme video
Masayuki Tezuka (Tokyo Institute of Technology, Japan) Keisuke Tanaka (Tokyo Institute of Technology, Japan) |
Session 2 - Symmetric Cipher
Session Chair: Wun-She Yap
|
Rotational-XOR Cryptanalysis of Simon-like Block Ciphers video
Jinyu Lu (National University of Defense Technology, China) Yunwen Liu (National University of Defense Technology, China) Tomer Ashur (TU Eindhoven, Netherlands) Bing Sun (National University of Defense Technology, China) Chao Li (National University of Defense Technology, China) |
|
A New Improved AES S-Box With Enhanced Properties video
Abderrahmane Nitaj (Universite de Caen Normandie, France) Willy Susilo (University of Wollongong, Australia) Joseph Tonien (University of Wollongong, Australia) |
|
Galaxy: A Family of Stream-Cipher-Based Space-Hard Ciphers video
Yuji Koike (University of Hyogo, Japan) Kosei Sakamoto (University of Hyogo, Japan) Takuya Hayashi (National Institute of Information and Communications Technology, Japan) Takanori Isobe (University of Hyogo, Japan) |
|
Automated Search for Block Cipher Differentials: A GPU-Accelerated Branch-and-Bound Algorithm video
Wei-Zhu Yeoh (Universiti Sains Malaysia, Malaysia) Je Sen Teh (Universiti Sains Malaysia, Malaysia) Jiageng Chen (Central China Normal University, China) |
Session 3 - Post-Quantum Cryptography
Session Chair: Muhammed Esgin
|
Optimized Arithmetic Operations for Isogeny-based Cryptography on Huff Curves video
Yan Huang (Sun Yat-sen University, Guangzhou, China) Fangguo Zhang (Sun Yat-sen University, Guangzhou, China) Zhi Hu (Sun Yat-sen University, Guangzhou, China) Zhijie Liu (Sun Yat-sen University, Guangzhou, China) |
|
On Lattice-Based Interactive Protocols with Aborts video
Nabil Alkeilani Alkadri (TU Darmstadt, Germany) Rachid El Bansarkhani (QuantiCor Security GmbH, Germany) Johannes Buchmann (TU Darmstadt, Germany) |
|
SKCN: Practical and Flexible Digital Signature from Module Lattice video
Boru Gong (Fudan University, China) Leixiao Cheng (Fudan University, China) Yunlei Zhao (Fudan University, China) |
|
Cloud-assisted Asynchronous Key Transport with Post-Quantum Security video
Gareth T. Davies (University of Wuppertal, Germany) Herman Galteland (Norwegian University of Science and Technology, Norway) Kristian Gjøsteen (Norwegian University of Science and Technology, Norway) Yao Jiang (Norwegian University of Science and Technology, Norway) |
Session 4 - Network Security and Blockchain
Session Chair: Jianfeng Wang
|
A Black-box Attack on Neural Networks Based on Swarm Evolutionary Algorithm video
Xiaolei Liu (China Academy of Engineering Physics, China) Teng Hu (University of Science and Technology of China, China) Kangyi Ding (University of Science and Technology of China, China) Yang Bai University of Science and Technology of China, China) Weina Niu (University of Electronic Science and Technology of China, China) Jiazhong Lu (Chengdu University of Information Technology, China) |
|
A Blockchain-based Resource Supervision Scheme for Edge Devices under Cloud-Fog-End Computing Model video
Tongchen Wang (Beihang University, China) Jianwei Liu (Beihang University, China) Dawei Li (Beihang University, China) Qianhong Wu (Beihang University, China) |
Session 5 - Attack
Session Chair: Jinguang Han
|
Rolling Attack: An Efficient Way to Reduce Armors of OA Devices video
Linyu Li (Chinese Academy of Sciences, China) Lei Yu (Chinese Academy of Sciences, China) Can Yang (Chinese Academy of Sciences, China) Jiawei Yin (Chinese Academy of Sciences, China) |
|
Improving Key Mismatch Attack on NewHope with Fewer Queries video
Satoshi Okada (University of Tokyo, Japan) Yuntao Wang (University of Tokyo, Japan) Tsuyoshi Takagi (University of Tokyo, Japan) |
|
A Novel Duplication Based Countermeasure To Statistical Ineffective Fault Analysis video
Anubhab Baksi (Nanyang Technological University, Singapore) Vinay B. Y. Kumar (Nanyang Technological University, Singapore) Banashri Karmakar (Indian Institute of Technology Bhilai, India) Shivam Bhasin (Temasek Labs@NTU, Singapore) Dhiman Saha (Indian Institute of Technology Bhilai, India) Anupam Chattopadhyay (Nanyang Technological University, Singapore) |
|
Design and Evaluation of Enumeration Attacks on Package Tracking Systems video
Hanbin Jang (Sungkyunkwan University, Korea) Woojoong Ji (Sungkyunkwan University, Korea) Simon S. Woo (Sungkyunkwan University, Korea) Hyoungshick Kim (Sungkyunkwan University, Korea) |
Session 6 - Privacy
Session Chair: Xingliang Yuan
|
JTaint: Finding Privacy-Leakage in Chrome Extensions video
Mengfei Xie (Wuhan University, China) Jianming Fu (Wuhan University, China) Jia He (Wuhan University, China) Chenke Luo (Wuhan University, China) Guojun Peng (Wuhan University. China) |
|
Unlinkable Updatable Databases and Oblivious Transfer with Access Control video
Aditya Damodaran (University of Luxembourg, Luxembourg) Alfredo Rial (University of Luxembourg, Luxembourg) |
Session 7 - Cryptographic Primitives
Session Chair: Shifeng Sun
|
SHOSVD: Secure Outsourcing of High-Order Singular Value Decomposition video
Jinrong Chen (National University of Defense Technology, China) Lin Liu (National University of Defense Technology, China) Rongmao Chen (National University of Defense Technology, China) Wei Peng (National University of Defense Technology, China) |
|
Efficient Forward-Secure Threshold Public Key Encryption video
Rafael Kurek (University of Wuppertal, Germany) |
|
A New Targeted Password Guessing Model video
Zhijie Xie (National University of Defense Technology, China) Min Zhang (National University of Defense Technology, China) Qiying Dong (Nankai University, China) Zhenhan Li (National University of Defense Technology, China) |
|
Multi-Input Laconic Function Evaluation video
Bo Pang (Chinese Academy of Sciences, China) Long Chen (New Jersey Institue of Technology, US) Xiong Fan (University of Maryland, US) Qiang Tang (New Jersey Institue of Technology, US) |
Session 8 - Mathematical Foundation
Session Chair: Man Ho Au
|
Arbitrary-Centered Discrete Gaussian Sampling over the Integers video
Yusong Du (Sun Yat-sen University, China) Baoying Fan (Sun Yat-sen University, China) Baodian Wei (Sun Yat-sen University, China) |
|
New Assumptions and Efficient Cryptosystems from the $e$-th Power Residue Symbol video
Xiaopeng Zhao (East China Normal University, China) Zhenfu Cao (East China Normal University, China) Xiaolei Dong (East China Normal University, China) Jun Shao (Zhejiang Gongshang University, China) Licheng Wang (Beijing University of Posts and Telecommunications, China) Zhusen Liu (East China Normal University, China) |
|
Revisiting the Hardness of Binary Error LWE video
Chao Sun (Kyoto University, Japan) Mehdi Tibouchi (NTT Secure Platform Laboratories, Japan) Masayuki Abe (NTT Secure Platform Laboratories, Japan) |
Session 9 - Machine Learning Security
Session Chair: Xingliang Yuan
|
PALOR: Poisoning Attacks against LOgistic Regression video
Jialin Wen (East China Normal University, China) Benjamin Zi Hao Zhao (University of New South Wales and Data61, Australia) Minhui Xue (The University of Adelaide, Australia) Haifeng Qian (East China Normal University, China) |
|
DeepCapture: Image Spam Detection Using Deep Learning and Data Augmentation video
Bedeuro Kim (Sungkyunkwan University, Korea) Abuadbba Sharif (Data61, Australia) Hyoungshick Kim (Sungkyunkwan University, Korea) |
Session 10 - Short Papers
Session Chair: Sushmita Ruj
|
Secure and Compact Elliptic Curve LR Scalar Multiplication video
Yaoan Jin (Osaka University, Japan) Atsuko Miyaji (Osaka University, Japan) |
|
User Identity Linkage across Social Networks via Community Preserving Network Embedding video
Xiaoyu Guo (PLA Information Engineering University, China) Yan Liu (PLA Information Engineering University, China) Xuzhong Wang (PLA Information Engineering University, China) Jing Chen (PLA Information Engineering University, China) |
|
Improvement of Fuzzy Identity-Based Encryption and Attribute-Based Encryption using Blakley Secret Sharin video
Zhe Xia (Wuhan University of Technology, China) Bo Yang (Shaanxi Normal University, China) Yanwei Zhou (Shaanxi Normal University, China) Mingwu Zhang (Hubei University of Technology, China) Yi Mu (Fujian Normal University, China) |
|
Recovering CRT-RSA Secret Keys from Noisy Square-and-Multiply Sequences in the Sliding Window Method video
Kento Oonishi (University of Tokyo, Japan) Noboru Kunihiro (University of Tsukuba, Japan) |
|
Security Analysis on Tangle-based Blockchain through Simulation video
Bozhi Wang (University of New South Wales and Data61, Australia) Qin Wang (Swinburne University of Technology and Data61, Australia) Shiping Chen (Data61, Australia) Yang Xiang (Swinburne University of Technology, Australia) |
|
Tightly Secure Chameleon Hash Functions in the Multi-User Setting and Their Applications video
Xiangyu Liu (Shanghai Jiao Tong University, China) Shengli Liu (Shanghai Jiao Tong University, China) Dawu Gu (Shan ghai Jiao Tong University, China) |